Understanding user privileges and how that affects the network is paramount in cybersecurity. The principle of least privilege (POLP) is defined as giving an account, user, or program the bare minimum regarding privileges; it should only be enough to perform its job and/or function. No matter how trustworthy or skilled a user or program may be, privileges should be limited to protect a network better.
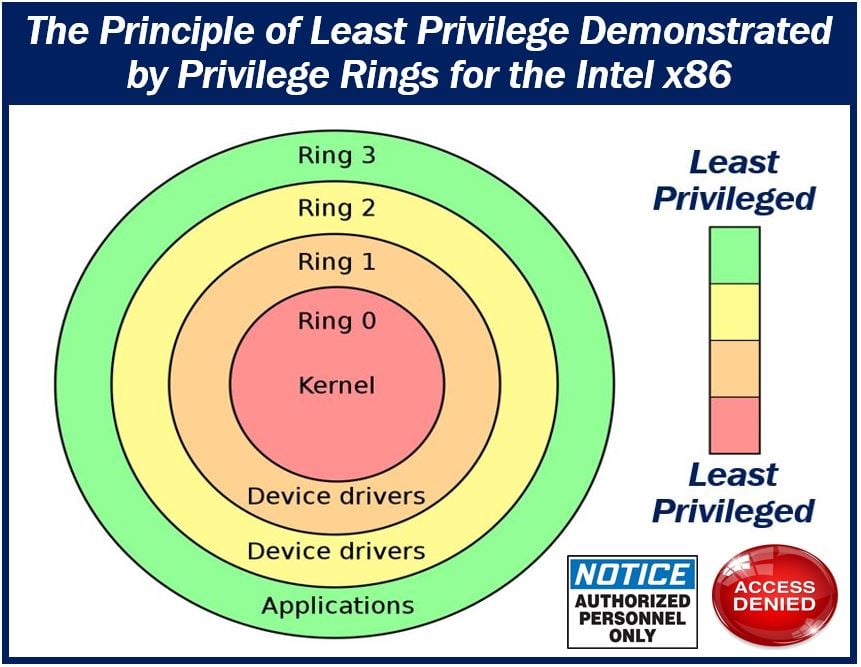
The benefit of the principle of least privilege is that it lowers the potential for discrepancies and anomalies within the network; this prevents potential Malware, data breaches, and other cybersecurity threats.
For the security principle of least privilege to remain effective, it is recommended that the following practices are used:
1. Properly Segment User Accounts
To make the most use of this principle, it is recommended that user accounts be segmented concerning access needed utilizing the following segmentations:
- User Accounts: These accounts are for regular users as they have the minimum amount of access to perform basic duties.
- Privileged Accounts: These accounts have elevated privileges; an example of this being administrative rights. The users within this group must perform higher-level tasks that require them to have these functions.
- Shared Accounts: While sharing an account is not typically recommended, and it may be necessary to allow a group of users to share an account. These accounts can consist of clients, business partners, contractors. Shared account users should only utilize the network for a brief period.
- Service Accounts: These accounts are not user-operated but are designed to allow applications to utilize specific privileges.
The accounts above allow only privileged groups to access higher network functions, meaning that user accounts are limited in what type of potential damage they may cause.
2. Manage Passwords
No matter what type of account is being used, it is essential that passwords are enforced as followed:
- Password Length: Passwords should be of a certain length to be more secure.
- Password Complexity: A mixture of capital and lowercase letters, symbols, and numbers should be required for each password.
- Password Age: A password should expire after a certain amount of time.
- Password History: It is recommended that the system is formatted to remember previous passwords, preventing reusing old passwords.
Carefully and effectively managing passwords allow users to have a more secure password every time they log in.
3. Delete and Manage Accounts When Necessary
One of the biggest issues that arise when it comes to the principle of least privilege is the lack of oversight when it comes to inactive or underregulated accounts. For example, in the case where an employee is fired from an organization or is moved to a position that does not require as many privileges, these changes to the respective accounts should be addressed immediately. The same can be true for programs, processes, and applications that are no longer used.
Each company should have an off-boarding process that reduces the risk of these accounts bringing harm to the network. Permission and access should be revoked or added in the case of a change in position; in some cases, it is deleted entirely.
4. Communicate Changes to the Wider Organization
It is not enough to implement these changes, but it is equally imperative to communicate these changes to the organization. Any organizational change is hard to process and implement. Being open and communicative about any changes to be made in an organization makes it more likely that these recommendations and procedures are followed.
By emphasizing POLP as a need for further security for the organization and the users themselves, users would be less likely to share access to accounts with those that do not have the necessary permissions.
5. Perform Audits regularly
Setting up accounts with the necessary privileges is essential for mitigating risk. Although these changes do help the security of the network, it is also recommended that audits are performed on accounts periodically. Some of the most common types of audits include the following:
- Usage Audits: Monitoring the data that is accessed, created, and deleted by users.
- Privilege Audits: Determine if a user still needs the privileges, they have access to.
- Change Audits: Examining any improper changes to an account’s permissions, settings, or passwords.
Using these best practices, the principle of least privilege can be effective in preventing security threats against the network. When you get to and maintain the security principle of least privilege, your entire system is less likely to be compromised.
Interesting related article: “What is cybersecurity?“

