Symantec Corporation says it has discovered an extremely sophisticated spying bug named Regin. According to the company, the backdoor Trojan is one of the most sophisticated pieces of malicious software it has ever come across.
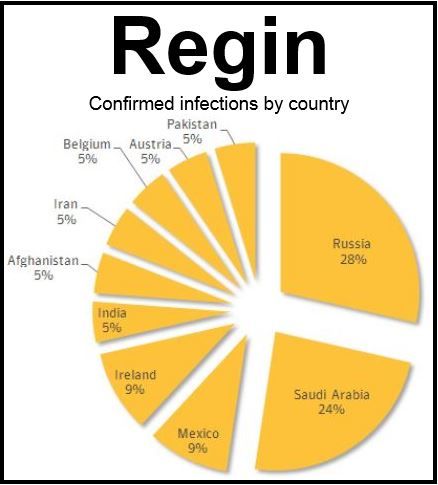
Computers in Saudi Arabia, Russia, Mexico and Ireland appear to be the most affected by the bug, which was most likely created by a government, given its complexity. Experts believe it has been in use for about six years and has hit several targets across the globe.
Symantec says the spying bug has been used to glean information from private individuals, businesses and government organizations.
As soon as it enters a computer it can steal passwords, capture screen shots and even recover files that have been deleted.
It must have been developed by a nation state, Symantec researchers believe, given the sophistication of its software.
It would have taken a long time to develop, maybe even years. Its creators have been very careful to make it virtually impossible to track.
70% of confirmed infections occurred in just Russia, S. Arabia, Mexico and Ireland.
According to Symantec security strategist, Sian John “It looks like it comes from a Western organization. It’s the level of skill and expertise, the length of time over which it was developed.”
Symantec researchers say the bug reminds them of a computer worm – Stuxnet – developed by Israel and the US to target Iran’s nuclear program.
While Stuxnet was made to destroy things, Regin appears to have been created to gather data.
In a 22-page report – “Regin: Top-tier espionage tool enables stealthy surveillance“ – the authors wrote:
“In the world of malware threats, only a few rare examples can truly be considered groundbreaking and almost peerless. What we have seen in Regin is just such a class of malware.”
Symantec says it is aware of two versions of Regin. Version 1.0 was likely used from at least 2008 to 2011, while Version 2.0 has been used since 2013 (maybe earlier).
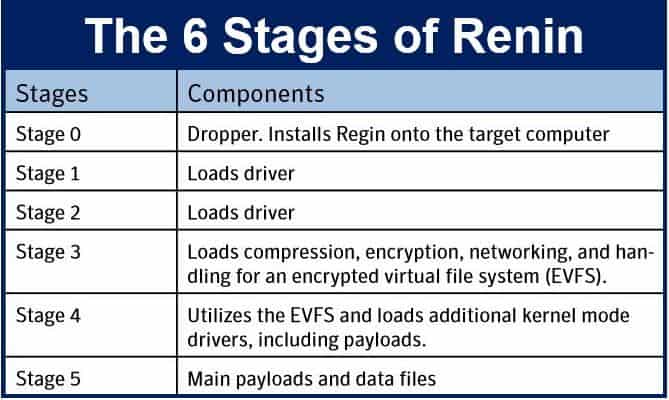
Regin has a six-stage architecture. Stage 1 and 2 involve installation and configuration of the threat’s internal services. Regin’s main payloads come into play in the later stages.
The Symantec researchers wrote:
“The most interesting stages are the executables and data files stored in Stages 4 and 5. The initial Stage 1 driver is the only plainly visible code on the computer. All the other stages are stored as encrypted data blobs, as a file or within a non-traditional file storage area such as the registry, extended attributes, or raw sectors at the end of disk.”