Let’s Encrypt found itself in quite a predicament earlier this month. On March 4, the certificate authority (CA) revoked millions of Secure Socket Layer (SSL) protocol certificates due to a flaw in its server software. The bug disrupted website owners’ ability to prevent unauthorized SSL certificate-issuing bodies from creating certificates for their domains. In short, it allowed any CA to issue a certificate to any domain without the prerequisite CA checks. That resulted in millions of duplicate SSL certificates for millions of sites.
As a marketing professional, you may be wondering how this incident can affect you. First and foremost, SSL certificates are essential because they tell users’ browsers that your site is secure. As you know, search engines favor HyperText Transfer Protocol Secure (HTTPS)-enabled sites. HTTPS goes hand in hand with the Transport Layer Security (TLS) protocol, SSL’s successor, which keeps data sent through HTTPS safe with encryption and authentication. With improperly configured SSL certificates, however, you may be unintentionally turning away visitors due to security red flags on your site.
If you suspect that your site has been affected by the Let’s Encrypt fiasco or are unsure if your site has an SSL certificate chain at all, you’ve come to the right place. In this post, we’ll delve into how a threat intelligence platform can verify if yours does and whether it’s configured correctly.
What Is SSL and How Does It Help?
SSL certificates are part of a trust infrastructure that comprises a chain link between an SSL certificate and a CA-issued root certificate. User agents, such as browsers, validate each certificate by checking for the signature of the CA succeeding it along with the SSL certificate’s public key. The verification path starts with the end user’s SSL certificate then goes through intermediate certificates that serve as proxies and ends with the root CA. The root CA is buried under layers of intermediate certificates to protect it from compromise.
Valid SSL certificates enable your site to establish encrypted HTTPS connections with your visitors. This function shields your users’ sensitive data from attackers who are keen on stealing or modifying them.
Besides, Google counts HTTPS as a ranking signal. It introduced this idea in 2014 when it encouraged site owners to migrate their web properties from HTTP to HTTPS. Though this may sound to some like a marketing ploy, there are some noticeable benefits. Some businesses reported doubling their number of high-ranking keywords after implementing HTTPS. Getting more eyeballs on your site, of course, leads to more conversion opportunities.
How to Use the Threat Intelligence Platform to Verify SSL Certificates
The Threat Intelligence Platform (TIP) retrieves all details about a domain’s SSL certificate and uncovers vulnerabilities they may have. In particular, it checks whether the intermediate certificates are on the same server as the SSL certificate. It also verifies if there’s a trusted root CA that issued the last certificate in the chain order. If there’s a certificate name mismatch or if the root CA doesn’t exist, errors would come up, preventing the requested page from displaying.
Let’s take a closer look at how the platform works. Using TIP, we looked into imtranslator[.]net, a site with an SSL certificate from Let’s Encrypt. Below are the results for its SSL certificate chain analysis.
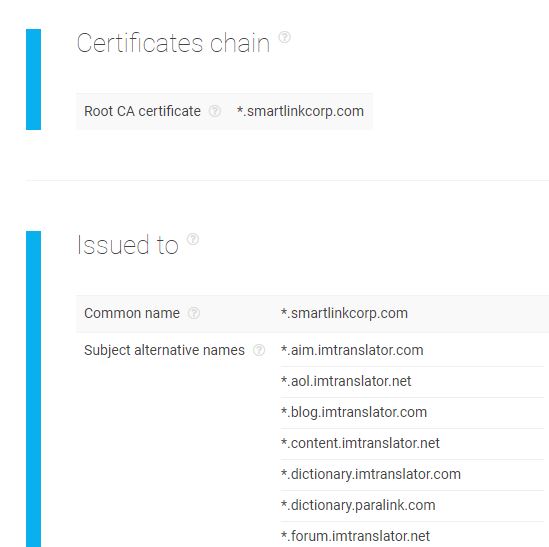 In the report above, we see that the root CA is smartlinkcorp[.]com, the company that owns iamtranslator[.]net and is in charge of its WHOIS records. That should come as no surprise since SSL certificates under the Let’s Encrypt program are self-signed and domain-validated. The analysis continues to a list of all domains authorized to use the SSL certificate.
In the report above, we see that the root CA is smartlinkcorp[.]com, the company that owns iamtranslator[.]net and is in charge of its WHOIS records. That should come as no surprise since SSL certificates under the Let’s Encrypt program are self-signed and domain-validated. The analysis continues to a list of all domains authorized to use the SSL certificate.
Is the certificate valid? Yes, because the tool did not find any inconsistencies in its documentation. The certificate also resides in the hostname’s server, as reflected in another section of the report.
 However, the SSL protocol settings presented a few misconfigurations. The host seems to support an outdated SSL connection version, which should be disabled and upgraded to TLS 1.2. The site also enables old forms of encryption and weak cipher keys that could potentially lead to chosen-plaintext attacks (CPAs). It also doesn’t automatically redirect users to an HTTPS version of the visited page (if they landed on its HTTP version). Webmasters might want to fix these issues.
However, the SSL protocol settings presented a few misconfigurations. The host seems to support an outdated SSL connection version, which should be disabled and upgraded to TLS 1.2. The site also enables old forms of encryption and weak cipher keys that could potentially lead to chosen-plaintext attacks (CPAs). It also doesn’t automatically redirect users to an HTTPS version of the visited page (if they landed on its HTTP version). Webmasters might want to fix these issues.
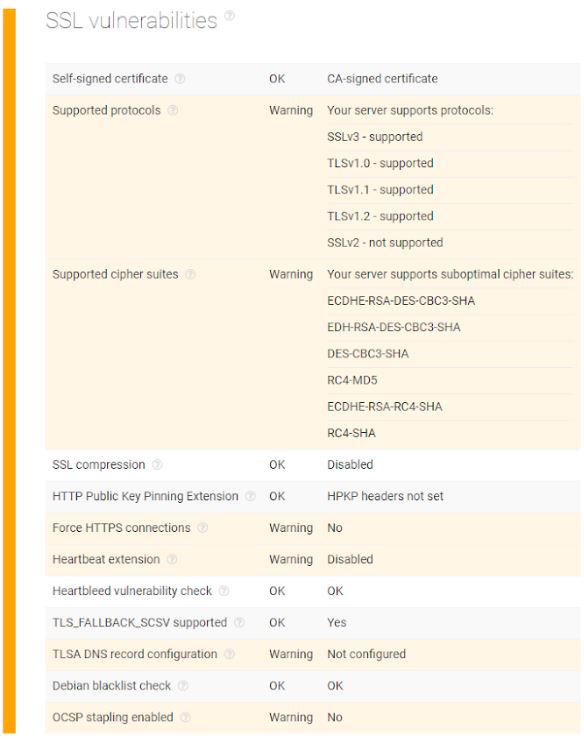 The exercise above illustrates how a threat intelligence platform assists in plugging SSL certificate chain loopholes. As long as it’s implemented accordingly, an SSL certificate keeps your and existing and potential customers’ data private, while ensuring continued traffic from your ideal audience.
The exercise above illustrates how a threat intelligence platform assists in plugging SSL certificate chain loopholes. As long as it’s implemented accordingly, an SSL certificate keeps your and existing and potential customers’ data private, while ensuring continued traffic from your ideal audience.
About the Author
 Jonathan Zhang is the founder and CEO of Threat Intelligence Platform (TIP)—a data, tool, and API provider that specializes in automated threat detection, security analysis, and threat intelligence solutions for Fortune 1000 and cybersecurity companies. TIP is part of the WhoisXML API family, a trusted intelligence vendor by over 50,000 clients.
Jonathan Zhang is the founder and CEO of Threat Intelligence Platform (TIP)—a data, tool, and API provider that specializes in automated threat detection, security analysis, and threat intelligence solutions for Fortune 1000 and cybersecurity companies. TIP is part of the WhoisXML API family, a trusted intelligence vendor by over 50,000 clients.
________________________________________________________________
Interesting related article: “What is Software?“

